Troubleshooting SAML Configuration via Azure Active Directory
This article walks through problems you might encounter after you have set up Single Sign On for your cloud instance following the steps in Legacy SAML Setup Guide for Microsoft Azure Active Directory.
If the Singe Sign On is not working as expected, please review the most common causes below, including how to verify them and how to fix it.
🔧 Problem during Basic SAML Configuration
Symptom
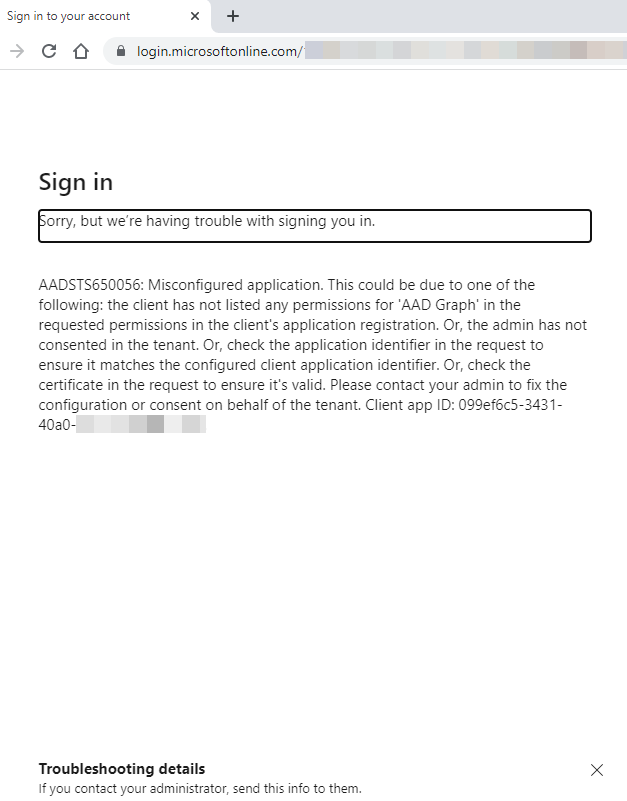
When trying to log in to iGrafx and you see an Azure AD error screen that looks similar to the following message:
| Misconfigured application. This could be due to one of the following: the client has not listed any permissions for AAD Graph in the requested permissions in the client's application registration. Or, the admin has not consented in the tenant. Or, check the application identifier in the request to ensure it matches the configured client application identifier. Or, check the certificate in the request to ensure it's valid. Please contact your admin to fix the configuration or consent on behalf of the tenant. Client app ID |
Potential Causes
One of the three URLs/Identifiers that make up the Basic SAML Configuration in your Azure Enterprise Application does not match the expected patterns. You can verify this by going to the iGrafx Azure Enterprise Application in your Azure Portal at https://portal.azure.com and opening the Single-Sign-On Tab, then looking at the Basic SAML Configuration section.
Fix
After navigating to the Basic SAML Configuration section, ensure the three items look as follows, including the https:// protocol prefix as well as the correct capitalization, and replacing %SUBDOMAIN% with your iGrafx subdomain:
Identifier (Entity ID)
https://%SUBDOMAIN%.igrafxcloud.com/saml/metadata
Reply URL (ACS URL)
https://%SUBDOMAIN%.igrafxcloud.com/saml/SSO
Sign on URL
https://%SUBDOMAIN%.igrafxcloud.com
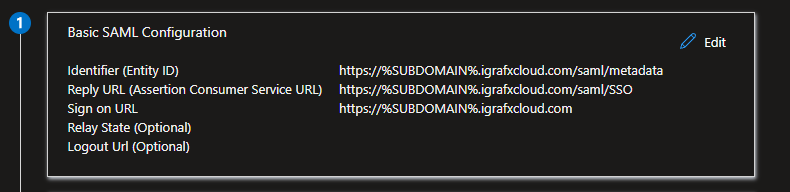
If any of the items does not look correct, click the pencil icon to edit it accordingly and save the changes
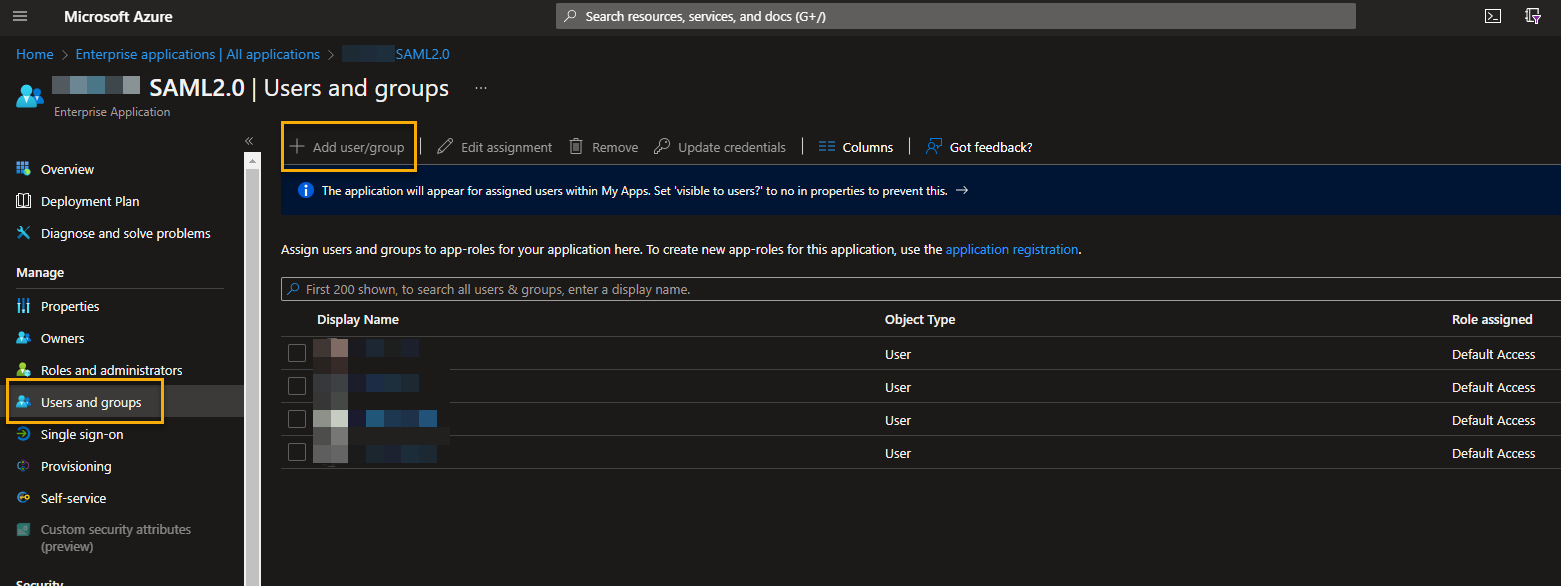
🔧 Problem with User and Group scopes
Symptom
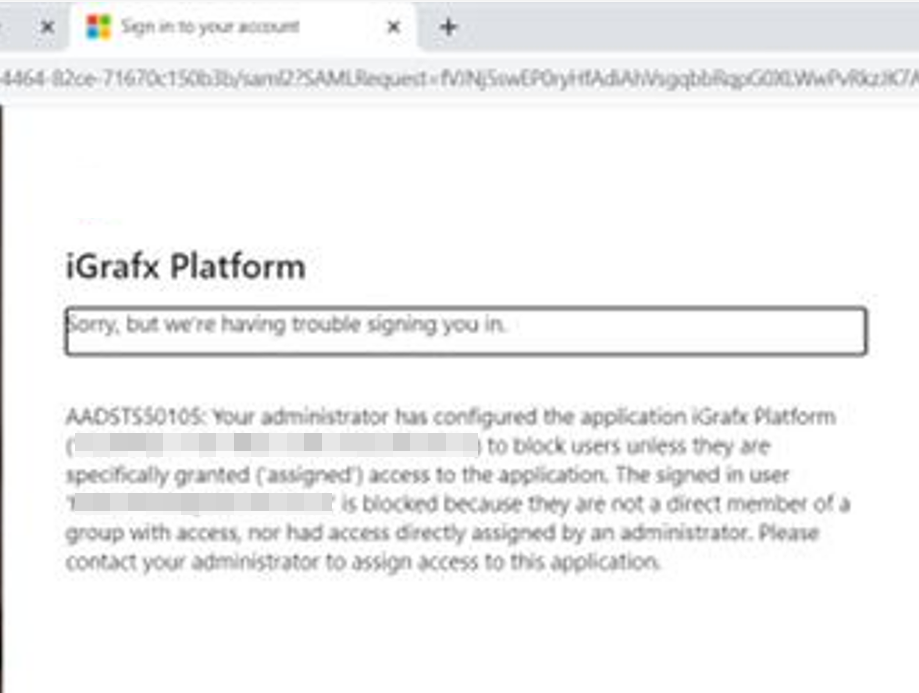
When trying to log in to iGrafx and you see an Azure AD error screen that looks similar to the following message, indicating that your user is not in scope for the Azure application:
| Your administrator has configured the application iGrafx Platform to block users unless they are specifically granted ("assigned") access to the application. The signed in user "username" is blocked because they are not a direct member of a group with access, nor had access directly assigned by an administrator. Please contact your administrator to assign access to this application. |
Potential Causes
This problem is caused by the user not directly or through one of the groups being configured to access the respective Azure Enterprise Application and can be fixed with in the Azure Portal.
Fix
Open your iGrafx Azure Enterprise Application in your Azure Portal at https://portal.azure.com and go to the Users and Groups blade. On the respective blade, you will see the list of directly assigned users and list of user groups that have access to the application. Make sure the user is a member of at least one of the groups or is directly assigned access to the application by clicking the Ad user/group button at the top.