ADFS Auto Creation of Authenticated Users
iGrafx Platform allows configuration of auto-creation of authenticated ADFS users in the iGrafx Platform. The following information and instructions pertain to SAML2 with ADFS. However, they can be used with modifications to do the same for other IDP's.
With SAML2 ADFS auto-creation configured correctly, an authenticated user who has not been defined/added in the iGrafx user table will be automatically created during the login process via an SSO-enabled login screen. A user entry in the Administration - User Management page will be created. If
If a user exists in the user table (User Management page), the matched users will be used mapped according to what has been defined for the 'Users' group (the 'Users' group must be added first in order to receive the auto-created authenticated users in the Administration – User Management page). If none or no default group is defined, then the user will be created, but no permissions will be granted, and you might receive a permission message.
Steps:
- Follow Microsoft ADFS Server steps above
- Enable Auto Creation of Authenticated users
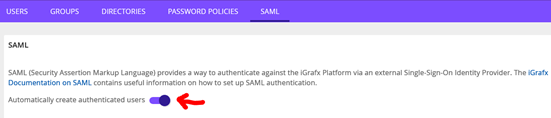
- Go to the platform Administration – User Management – SAML page
Click button (Automatically create authenticated users) to enable (See below)
- Determine ADFS Rule Language (URLs) for email, first name, and last name (Aka SAML Attributes)
There are two methods that can be used to determine the correct rule languages/SAML Attributes for first name, last name, and email, direct and indirect.- Direct - contact the SSO ADFS team to request these rule language URLs
- Enter the following in the ADFS Edit Rule LDAP Attribute tab
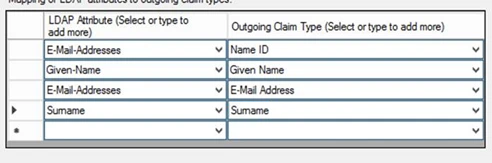
Check generated rule languages – an example is shown below:
CODEc:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname"), query = ";sAMAccountName,givenName,mail,sn;{0}", param = c.Value);
- Enter the following in the ADFS Edit Rule LDAP Attribute tab
- Indirect - using logged messages in the Platform
- Change logging level to 'DEBUG' in the Support- Logging Settings tab page
- Inactivate/disable 'Log All Classes'
- Check ‘Custom’ radio button and enter org.springframework.security.saml;org.opensaml;PROTOCOL_MESSAGE
- Ask a user with a Windows logon user id to login iGrafx platform
- Go to the System Log tab and copy the text in the window
- Analyze the logged messages to local rule language URLs/SAML attributes. If you cannot find any rule language URLs, then maybe they are encrypted, then use Direct Method instead.
An example of log messages containing these edited language URLs is shown below.
CODE<Subject><NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">user@igrafx.com</NameID> <SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <SubjectConfirmationData InResponseTo="aba86j6216if75f4g52jfidjf0ddej" NotOnOrAfter="2018-02-06T15:58:42.048Z" Recipient="https://www.igrafx.com:443/saml/SSO"/> </SubjectConfirmation> </Subject> <Conditions NotBefore="2018-02-06T15:48:42.048Z" NotOnOrAfter="2018-02-06T16:48:42.048Z"> <AudienceRestriction> <Audience>https://icorp.igrafx.com/saml/metadata</Audience> </AudienceRestriction> </Conditions> <AttributeStatement> <Attribute Name="http://schemas.microsoft.com/identity/claims/tenantid"> <AttributeValue>xxx</AttributeValue> </Attribute> <Attribute Name="http://schemas.microsoft.com/identity/claims/objectidentifier"> <AttributeValue>xxx</AttributeValue> </Attribute> <Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"> <AttributeValue>user@igrafx.com</AttributeValue> </Attribute> <Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname"> <AttributeValue>LastName</AttributeValue> </Attribute> <Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname"> <AttributeValue>FirstName</AttributeValue> </Attribute> <Attribute Name="http://schemas.microsoft.com/identity/claims/identityprovider"> <AttributeValue>https://sts.windows.net/xxx/</AttributeValue></Attribute> </Attribute> ...
- Direct - contact the SSO ADFS team to request these rule language URLs
Enter Rule Languages in iGrafx Platform – Administration – User Management –SAML page
Go to the iGrafx Platform – Administration – User Management – SAML tab and enter the rule language URLs as shown here.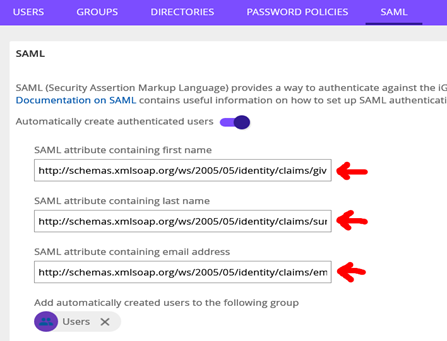 CODE
CODESAML attribute containing first name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname SAML attribute containing last name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname SAML attribute containing email address http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress- Restart service
