Roles and Permissions
The iGrafx Platform consists of a server instance which can contain one or more repositories. Within each repository there are repository items consisting of diagrams, enterprise objects (e.g. Resources, Strategies, etc.), non-iGrafx files (e.g. Office Word documents) and folders to help organize the content. Access to the server, repositories, and items is controlled with licenses, roles, and permissions. This document focuses on roles and permissions and item role assignments. The diagram below gives an overview of the relationships between users, groups of users, permissions, roles, and components controlled. As you can see in the diagram a role is a set of permissions which can be assigned to a group or individual user. Each item, repository, and server role has a set of permissions that can be granted, vetoed or left unspecified.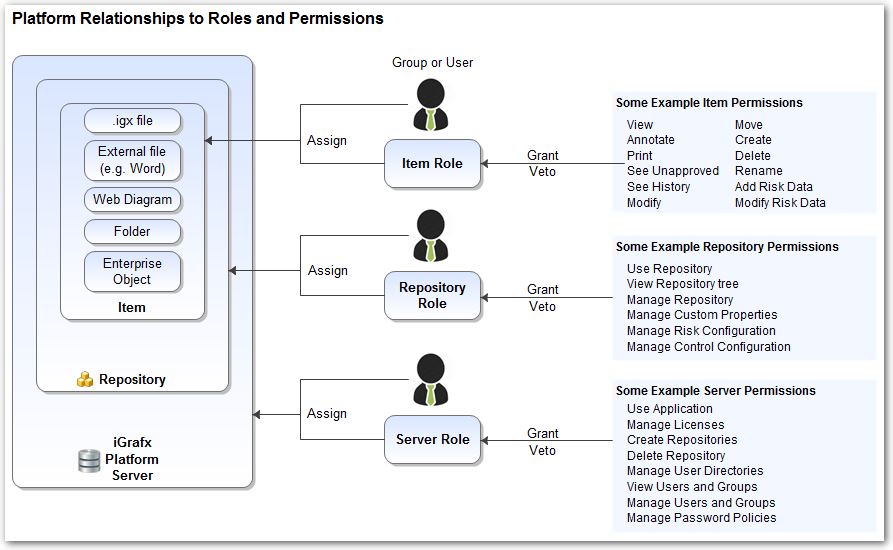
Controlling Access to a Repository Item
Access to repository items is controlled on the item's Permissions tab. A repository item can be an iGrafx file, a non-iGrafx file, a Web Diagram, a Folder, or an Enterprise Object. Within the Permissions tab of the item, control access by granting users or groups an applicable role for an item. For example, to give the "Marketing" group the Author role on a repository item:
- Select an item in the repository for which the permissions need to change
- Click the PERMISSIONS tab (right hand side)
Click ASSIGN ROLE TO USER/GROUP
If you do not see the ASSIGN ROLE TO USER/GROUP button then you do not have adequate permissions to perform the command on this item.- Search and select the name of the specific individual or group for which the required permission needs to be set (e.g. "Marketing"). Once selected, click CONTINUE.
- Search and select the applicable Role (e.g. "Author") that you want to grant to the selected user or group, as it relates to the item selected in step 1
- Click FINISH and expand the Marketing row
In this example, the screenshot shows that "Marketing" has the "Author" role for the selected item.
Inherited Role Assignments
- Select a repository item (e.g. a Folder) that contains one or more child items
- Perform steps 1 through 6 in the above topic
- Select one of the child items and choose the PERMISSIONS tab (if not currently displayed)
- Expand the Marketing assignment as shown below
In this example, the screenshot shows that "Marketing" has the "Author" role based on an inherited role assignment on a parent object. Clicking the arrow will display the parent where the role assignment was made.
View Effective Permissions
After performing the above steps, if Jane Smith is a member of the "Marketing" group, she should now have Author permissions for the item and its children. This can be confirmed by following these steps:
- If not already visible, display the item PERMISSIONS tab
- Click VIEW EFFECTIVE PERMISSIONS
- In the edit field, type a user name (e.g. "Jane") and then choose that user from the list
- Click SHOW WHY
All available item permissions are displayed. In our example, Jane will probably have all permissions granted by the Author role assignment. However, other item role assignments (e.g. to other Groups Jane is a member of) may override the Author role assignment. The next topic discusses combined permissions. See the Item Permissions and their Definitions topic to understand the meaning of each permission.
During an Approval Cycle, an exception is made to the permission rules. If a user without "See Unapproved" item permission is asked to approve a non-approved item then they will be allowed to do so. By including a user in the Approval Cycle Group, they are granted temporary permission to view unapproved versions.
Evaluating Combined Item Permissions
A user’s effective permissions for an item are primarily determined by role assignments for the user (or groups the user belongs to) on an item or the item’s parents. This allows needed control over repository content. For example, an organization could give a group of ‘Authors’ access to a repository folder, but restrict that group’s access to other repository content. Imagine a company with authors in the Accounting and Marketing groups. Each group can add and edit iGrafx diagrams in their assigned repository folder but are not allowed to view repository content outside their dedicated folders. To implement this configuration, the administrator assigns the “None” item role to both the Accounting and Marketing groups on the repository root object.
Further down the hierarchy, on the “Accounting Processes” folder, the Accounting group is assigned the Author role. On the “Marketing Processes” folder, the Marketing group is assigned the Author role. Now, members of each group can only author in their folder (and its sub-folders) while not seeing other repository content. Assigning roles in the Platform typically gives intuitive results like the example above where group role assignments on an item override group role assignments of an items parent.
Be aware, however, that permissions are calculated separately for the user and each group the user belongs to and then combined to determine the final effective permissions for an item. Therefore, it may be necessary to understand the details for setting effective permissions documented below. This procedure is supplemented with a flowchart and permissions table on the following pages.
Determining Item Permissions
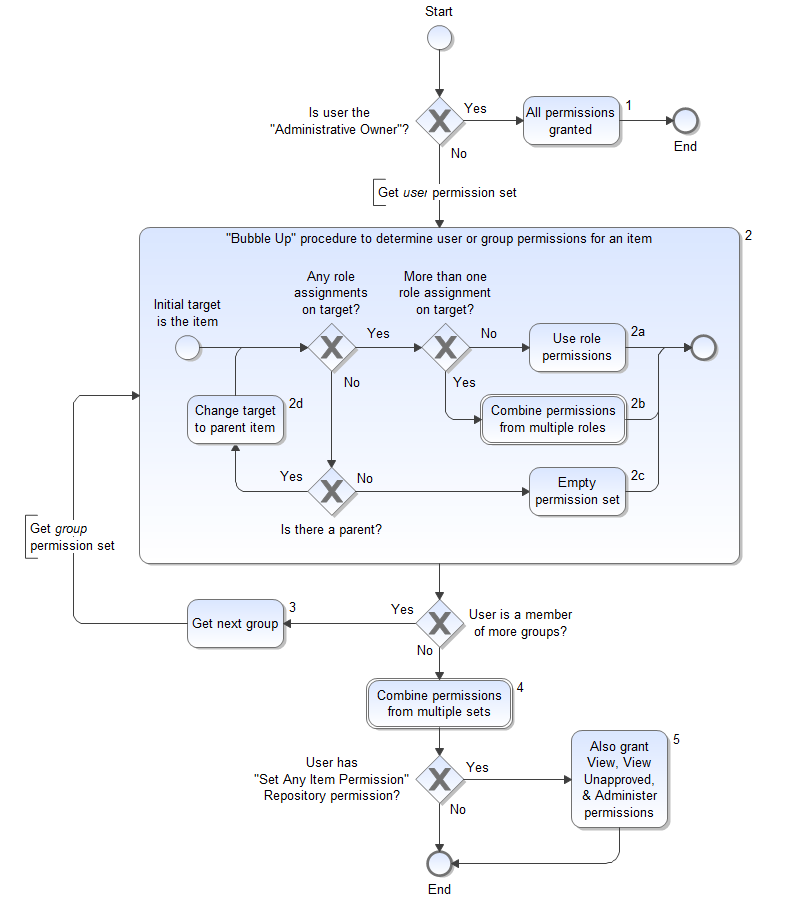
Main procedure:
- If the user is the “Administrative Owner” of the item, then the user has every permission on the item (shape #1 on Permissions Flowchart). Otherwise proceed to the next bullet.
- Follow the "Bubble Up" procedure (the large shape #2) described below for the user and, separately, for every group (shape #3) the user belongs to. This determines a permission-set for the specific user and a permission-set for each group the user belongs to.
- Combine the permission-sets (shape #4) as specified by the Permissions Table (displayed after the flowchart): a specific permission is granted if any of the permission-sets grant it and none deny it.
- If the user has the special "Set Any Item Permission" repository-level permission, then also grant the user (if not already granted) “View”, “View unapproved”, and “Administer” permissions (shape #5).
“Bubble Up” procedure:
Work your way up the repository tree from the item to the root, and stop when you find an item with any role assignments for the user or group the user belongs to:
- Does the user or group have one or more role assignments on the item? If yes, then use the role permissions (shape #2a) or combine multiple role permissions (shape #2b) as determined by the Permissions Table and return the result. If not, continue to the next bullet.
- Does the item have a parent? If not, return an empty (no grants and no denies) permission-set (shape #2c).
- Change the item to inspect to the item's parent (shape #2d).
Permissions Flowchart
Permissions Table
For any permission (e.g. Modify, Create, etc.), this table displays the user’s effective permission when multiple permission sets are combined (shapes #2b and #4 in Permissions Flowchart) for a repository item:
| Given these permission combinations: | The resulting combined permission: | |||
|---|---|---|---|---|
| = | ||||
| = | ||||
| Unspecified | = | |||
| = | ||||
| Unspecified | = | |||
| Unspecified | = | |||
| = | ||||
| = | ||||
| Unspecified | Unspecified | = | ||
| Unspecified | = | |||
Examples of Combined and Hierarchical Permissions
These examples give the results of various combinations of item role assignments in a repository hierarchy. For all the examples, assume the following:
- The “Order Entry” diagram is in the “Marketing Processes” folder
- Jane belongs to the “Marketing” group
- The default permissions are defined for the roles shown
Group role assignment:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | None | |
| “Marketing Processes” folder | ||
| “Order Entry” diagram |
Result: Jane has no effective permissions on the “Order Entry” diagram.
Group role assignments:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | None | |
| “Marketing Processes” folder | Author | |
| “Order Entry” diagram |
Result: Jane’s effective permissions on the “Order Entry” diagram are equivalent to Author permissions.
User and Group role assignments:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | None | |
| “Marketing Processes” folder | Author | |
| “Order Entry” diagram |
Result: Jane’s effective permissions on the “Order Entry” diagram are equivalent to Author permissions.
User role assignments:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | ||
| “Marketing Processes” folder | Author | |
| “Order Entry” diagram |
Result: Jane’s effective permissions on the “Order Entry” diagram are equivalent to Author permissions.
Combined user and group role assignments:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | Deny all | |
| “Marketing Processes” folder | Administrator | |
| “Order Entry” diagram |
Result: Jane has no effective permissions on the “Order Entry” diagram. Her effective permissions are a combination of the Administrator and Deny all roles. Because the Deny all role vetoes all permissions, Jane has no effective permissions.
Combined group role assignments:
In this example, Jane is a member of both the “Marketing Admin” and “Marketing” groups and there are no user role assignments.
| Item | Roles for “Marketing Admin” group | Roles for “Marketing” group |
|---|---|---|
| Root folder | Deny all | |
| “Marketing Processes” folder | Administrator | |
| “Order Entry” diagram |
Result: Jane has no effective permissions on the “Order Entry” diagram for the same reasons given in the previous example.
Group role assignments:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | Deny all | |
| “Marketing Processes” folder | Administrator | |
| “Order Entry” diagram |
Result: Jane’s effective permissions on the “Order Entry” diagram are equivalent to Administrator permissions.
Jane is denied:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | Administrator | |
| “Marketing Processes” folder | None | |
| “Order Entry” diagram | Deny all |
Result: Jane has no effective permissions on the “Order Entry” diagram. Her effective permissions are a combination of the Deny all, and None roles. Because the Deny all role vetoes all permissions, Jane has no effective permissions.
Jane is administrator:
| Item | Roles for Jane | Roles for “Marketing” group |
|---|---|---|
| Root folder | Viewer, Author | |
| “Marketing Processes” folder | Deny all | |
| “Order Entry” diagram | Administrator |
Result: Jane has administrator permissions on the “Order Entry” diagram. Her effective permissions are a combination of the Administrator, Viewer, and Author roles. The Deny all role assignment is ignored.
Jane is denied with "Everybody" role assignment:
| Item | Roles for Jane | Roles for “Everybody” group |
|---|---|---|
| Root folder | Author | |
| “Marketing Processes” folder | None | |
| “Order Entry” diagram |
Result: Jane has no effective permissions on the “Order Entry” diagram. Her effective permissions are the result of the None role assignment on "Marketing Processes." Because the role assignments are on the same group, "Everybody", the two assignments are not combined and the role assignment on the Root folder is ignored.
Server Permissions and their Definitions
These permissions are available for the iGrafx Platform server instance.
| Permission | Definition |
|---|---|
| Use Application | Required to log in. |
| Manage Licenses | Access and use the Administration Area / License page which includes License Management (e.g. Activate New License) and License Assignment tabs. Access the License Management tabs even if no license is activated or user licenses are over allocated. |
| Create Repositories | Create repositories, register repositories and view repository settings. |
| Delete Repository | Delete repositories, unregister repositories and view repository settings. |
| Manage User Directories | Access the Administration Area / User Management page / Directories tab which includes the “Add New Directory” command. |
| View Users and Groups | Access the Administration Area / User Management page to view existing Users and Groups. If a user has “Manage Users and Groups” Permission then they can view Users and Groups regardless of this permission. |
| Manage Users and Groups | Access the Administration Area / User Management page / Users tab (Create, Edit, Disable and Delete User) and Groups tab (Create, Rename, and Delete Group). |
| Manage Password Policies | Access the Administration Area / User Management page / Password Policies tab where these password complexity settings are made:
|
| Assign Server Roles | Access the Access the Administration Area / Security Roles / Server Role Assignments tab where Users are assigned Server Roles. |
| Edit Server Settings | Access the Administration / Server Setting pages where server configuration, email settings, database settings, video providers, early access and check for software updates is performed. |
| Manage Server Roles | Access the Administration Area / Security Roles / Server Roles tab (permissions are Granted, Unset, or Vetoed on Server Roles) and Server Role Assignments tab (Users assigned Server Roles). |
| Manage Repository Roles | Access the Administration Area / Security Roles / Repository Roles tab (permissions are Granted, Unset, or Vetoed on Repository Roles) and Repository Role Assignments tab (Users assigned Repository Roles). |
| Manage Item Roles | Access the Administration Area / Security Roles / Item Roles tab where permissions are Granted, Unset, or Vetoed on Item Roles. |
| Can Customize | Access the Administration Area with commands for these topics:
|
| Access Support Features | Access the Administration Area / Support page with commands for these topics:
|
| Can Report Issues | Access the "Contact Support" link in the main navigation bar. |
| Access REST API | Access the REST API tab in the Administration Area, Support page. |
Repository Permissions and their Definitions
Each of these Permissions is specific to one or more repositories.
| Permission | Definition |
|---|---|
| Use Repository | Required to view or edit the repository in the Model area. |
| View Repository Tree | Access a hierarchical tree view of repository content. Without this permission, it is still possible to view /edit content via object lists, search, breadcrumbs, links, etc. |
| Manage Repository | Access these pages in the Configuration Area:
|
| Manage Cycle Groups | Access the "Cycle Groups" page in the Configuration Area. |
| Manage Custom Properties | Access the "Custom Properties" page in the Configuration Area. |
| Manage Risk Configuration | Access the "Risks" page in the Configuration Area. |
| Manage Opportunity Configuration | Access the "Opportunities" page in the Configuration Area. |
| Manage Control Configuration | Access the "Controls" page in the Configuration Area. |
| Manage Performance Indicator Configuration | Access the "Performance Indicators" page in the Configuration Area. |
| Manage Journey Configuration | Access the "Journey" page in the Configuration Area. |
| Manage Capability Configuration | Access the "Capability" page in the Configuration Area. |
| Add Performance Indicator Data | Required to add new data entries on Performance Indicator objects. |
| Modify Performance Indicator Data | Required to edit or delete data entries on Performance Indicator objects. |
| Assign Repository Roles | Access the Access the Administration Area / Security Roles / Repository Role Assignments tab where Users are assigned Repository Roles. |
| Set Any Item Permissions | For repository items, the “Assign Role to User / Group” command is available on the Permissions tab. |
| Allow Bulk Approvals | Users with this role can select multiple approval items in their To-do list and approve them together. |
| View All Deleted Objects | When enabled allows users to see objects that are deleted by others users in the Recycle Bin. Also enables permission to empty the recycle bin for all items for all users. |
Item Permissions and their Definitions
The table below gives detailed descriptions of the provided repository Item permissions.
| Permission | Definition |
|---|---|
| View | See items in the repository tree and search and query results. Users who do not have View permissions on a folder in the tree cannot see the folder, even if they have view permissions for some items within the folder. |
| View Diagram Comments | View diagram comments made by you or a colleague. |
| Add Diagram Comments | Add comments to repository diagram. |
| Modify Own Diagram Comments | Edit your comments on a repository diagram. |
| Delete Own Diagram Comments | Delete your comments on a repository diagram. |
| Move Any Diagram Comments | Within a diagram, move the location of any comment. |
| Delete Any Diagram Comments | Delete any comments on a repository diagram. |
| Publish or print an item. | |
| See Unapproved | See and retrieve unapproved versions of an item. If a user does not have this permission, they cannot see items that do not have any approved versions. If they have “See History” permission, they can only see previously approved versions. |
| See History | See (and retrieve from) the history of an item. Depending on the See Unapproved permission, the history shows only approved versions, or all versions. This permission also enables the View Labeled Version command. |
| Modify | Check out and check in documents, diagrams, and components. Does not apply to folders. The user can modify project status for items owned by them. If their modify rights are revoked while an item is checked out, they can choose the Undo Check Out command, but cannot check in the item. |
| Move | Move an object to a different folder. Create permission is required on the destination folder. Delete permission is not required on the source folder or object. |
| Create | Add new items to a folder. |
| Delete | Delete an item from the repository. |
| Rename | Rename an item in the repository. |
| Review | In a Review Cycle, permission to review an item. |
| Approve | In an Approve Cycle, permission to vote to approve an item. |
| Endorse | In an Endorse Cycle, permission to endorse an item. |
| Add Risk Data | Add values to a risk or risk instances. |
| Modify Risk Data | Modify or delete existing values on a risk or risk instance. |
| Modify Project Status | Change project status parameters in the client Repository Item Properties dialog box, Repository Properties page, Project Status tab for an item you do not own. |
| Set Reviewers | Add, change, or delete users in review cycles. This permission does not provide the ability to start review cycles. |
| Set Approvers | Add, change, or delete users in approval cycles. This permission does not provide the ability to start approval cycles. |
| Set Endorsers | Add, change, or delete users in endorsement cycles. This permission does not provide the ability to start endorsement cycles. |
| Manage Review Cycle | Schedule review cycles. Start review cycles. |
| Manage Approval Cycle | Schedule approval cycles. Start approval cycles. |
| Manage Endorsement Cycle | Schedule endorsement cycles. Start endorsement cycles. |
| Manage Elective Watchers | Enable the ADD ELECTIVE WATCHER(S) command for an object and the ability to remove elective watchers. |
| Manage Required Watchers | Enable the ADD REQUIRED WATCHER(S) command for an object and the ability to remove required watchers. |
| Administer |
|
This article contains

